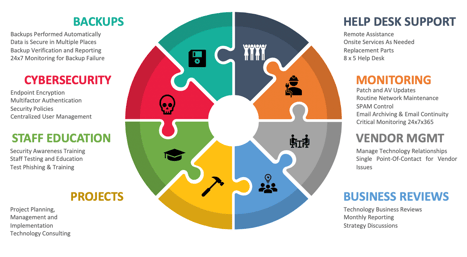
CPT takes a proactive approach, no matter if we are the sole IT support provider or working in a co-managed model. We have the resources, flexibility and experience to do both!
Fully
Co Managed
to create a partnership to supplement, enhance and support your existing IT team.

All-inclusive IT Services
No Hidden Costs. Truly Flat Rate, Predictable IT.

Now is the time to ensure that your sensitive data
is protected.
No organization is safe from a cyber attack, regardless of size or location.
Traditional antivirus can no longer keep up with today’s threats. Having a firewall is simply not enough. Our security package combined with 24/7/365 expert monitoring delivers a complete and robust response solution.
-
Secure Management
Manage and administer user access standards, security policies
and procedures. -
Secure Access
Identify threat like behavior such as impossible logins, multi-factor
bypass, coordinated attacks, and rogue agents. -
Secure Services
Monitor, detect, analyze and respond to security threats in real-time,
to proactively manage vulnerabilities. -
Secure Endpoint
Protect every entry point with a layered approach to safeguard
against malware and other threat attempts. -
Secure Email
Email protection through encryption, decryption and scanning of
emails for phishing, spam, viruses and anomalies.
.png?width=967&height=811&name=Untitled%20design%20(49).png)
We're proud to partner with the best in the industry




